#configuration
-
Import Pulseway configuration from command line
- 13 comments
- 26036 views
-
iOS 9 Pulseway update and "Unknown connection error" message
- 1 comment
- 13285 views
-
Servers using SHA-1 SSL Certificates
- 1 comment
- 6940 views
-
Contract for Limited Service Offered to A Client
- 3 comments
- 1376 views
-
Allow Windows 11 Upgrade in my Patch Management Policy
- 4 comments
- 1353 views
-
How to Manage Pending and Rejected Updates💡
- 1 comment
- 1055 views
-
Only manage 3rd party updates
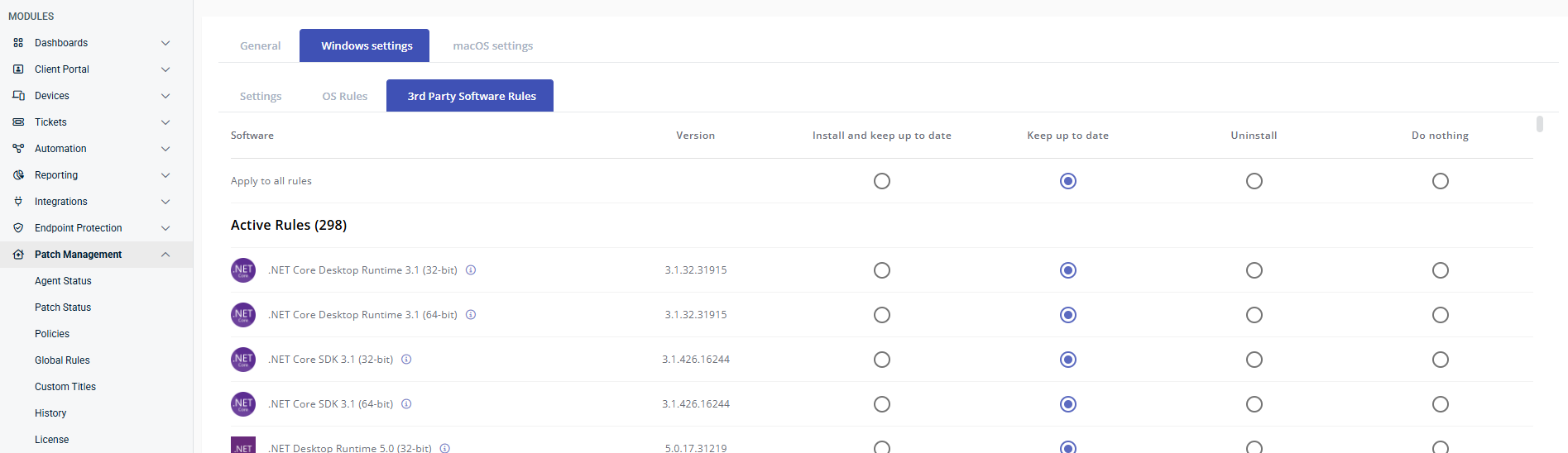
- 2 comments
- 1234 views
-
Devices... Roles... Cannot Remove/Edit a role nor delete a listed server
-
Change password and deploy it
- 3 comments
- 4268 views
-
Disable Services monitoring for specific Services
- 8 comments
- 8213 views
-
White-label end-user RMM applications for MSP's
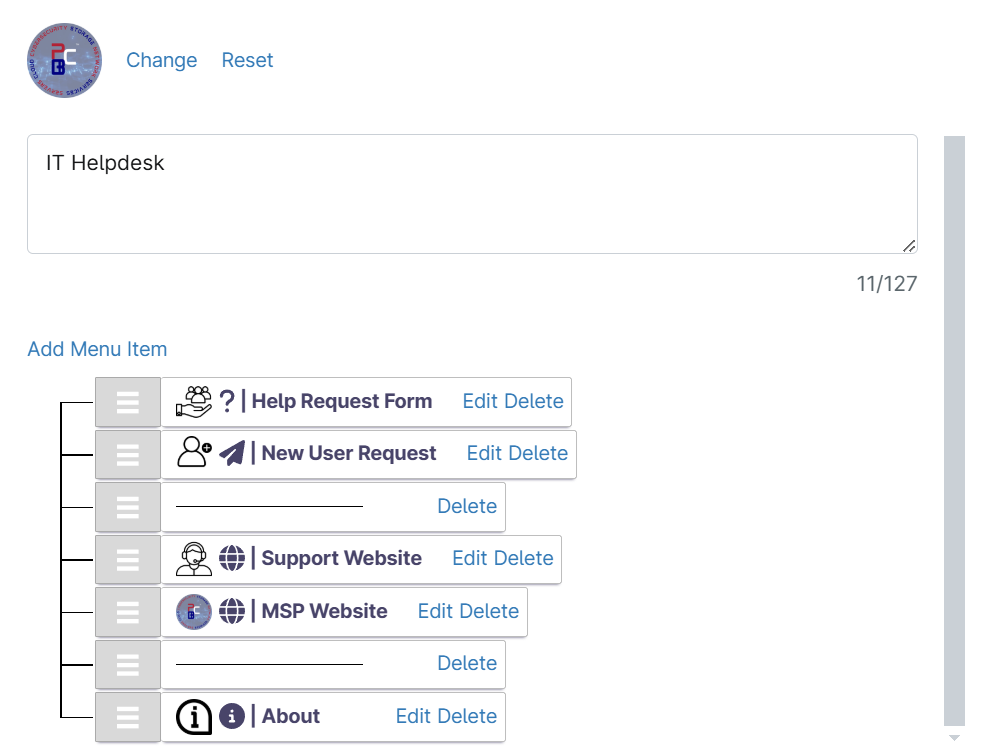
- 2 comments
- 992 views
-
Get Alert in Email when Remote access to a device
- 2 comments
- 1451 views
-
Request for help! Trying to record local admin group memberships for all systems
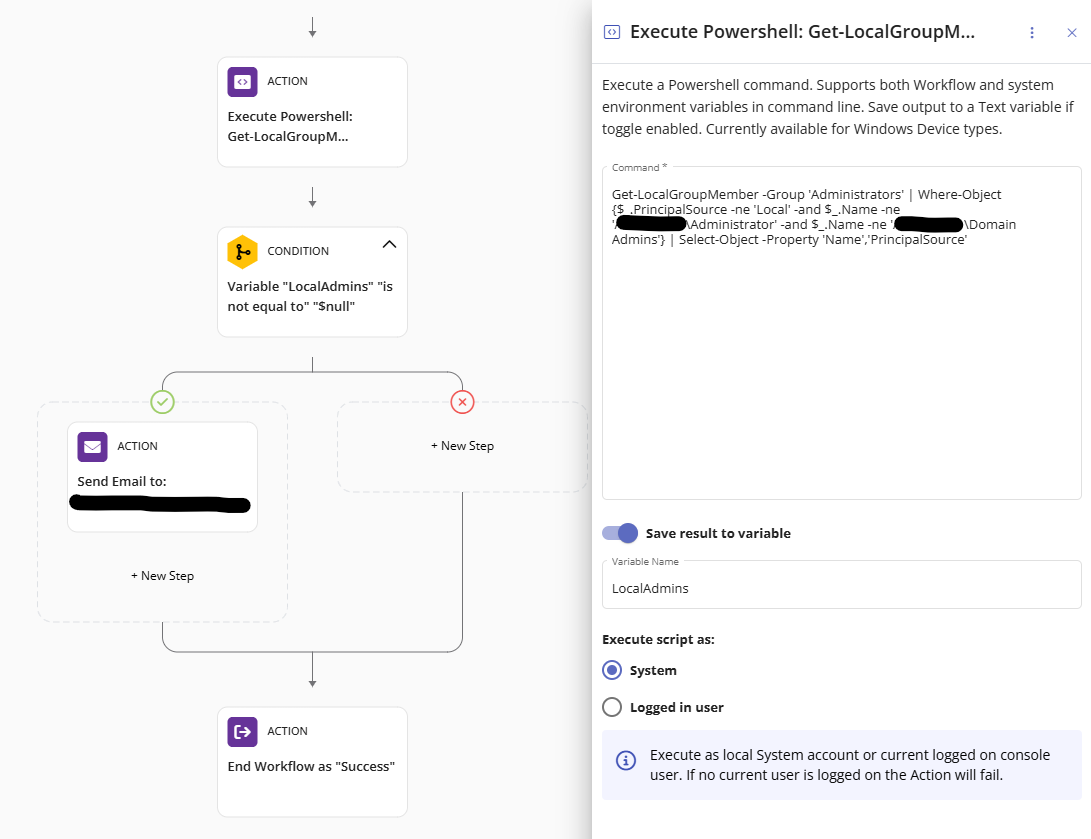 Marc Lye ·
Marc Lye ·- 2 comments
- 1444 views
-
Dashboard re-authentication
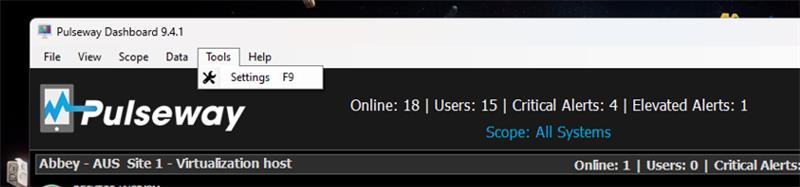
- 9 comments
- 3868 views
-
Patch Management prompt text incomplete
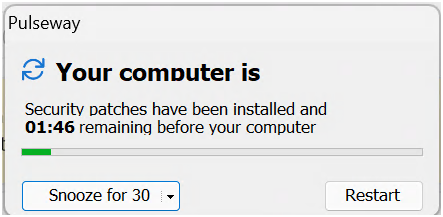
- 1 comment
- 776 views
-
Could Someone Give me Advice on Optimizing Pulseway for Remote IT Management?
-
Need some guidance as in what category should I participate into?
besoss ·
- 2 comments
- 1346 views
-
SNMP Printer Supply Levels
- 1 comment
- 1391 views
-
Notification email for already closed tickets
- 2 comments
- 1171 views
-
1-Click
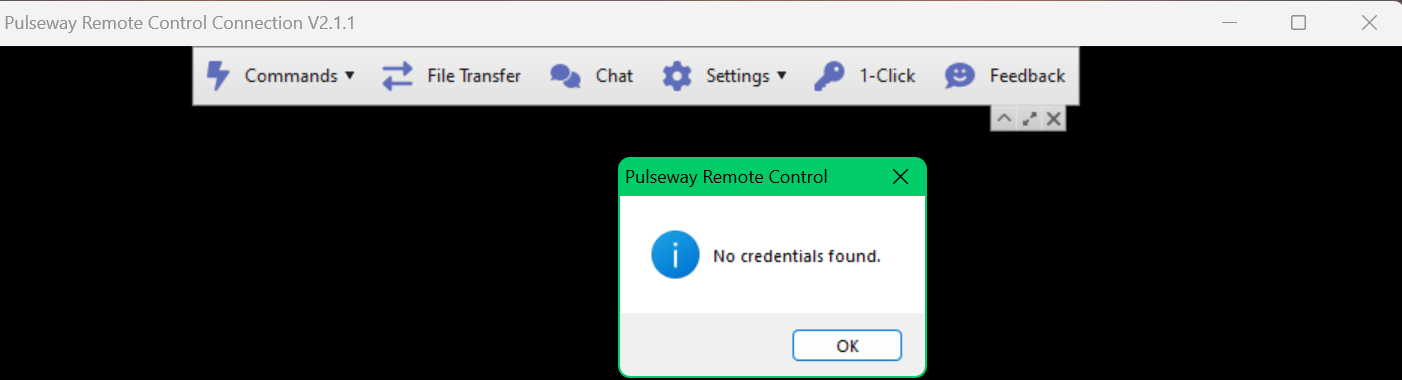
- 6 comments
- 5182 views
_a9c1b4.png)
_49ee3f.png)

