All Activity
- Yesterday
-
pcs server joined the community
- Last week
- How to transfer files without remoting into a device 🖥️
-
guest joined the community
-
test12 joined the community
-
DarienAL started following How to transfer files without remoting into a device 🖥️
- How to transfer files without remoting into a device 🖥️
-
How to transfer files without remoting into a device 🖥️
You know that moment when you realize you’ve been doing something the hard way for years? Here’s how to upload and download files without opening a remote session: Open the device card for the machine you want to access Head to the Storage tab You’ll now see Upload and Download options (yep, both!) Upload any file or folder directly to the device Download files off the device—downloads as a ZIP, easy to extract This feature works on Windows, macOS, and Linux! Bonus: Use automation workflows to push files across multiple machines 💥
-
 Jan C. Nielsen reacted to a post in a topic:
Pending file operation which requires a reboot to complete
Jan C. Nielsen reacted to a post in a topic:
Pending file operation which requires a reboot to complete
-
 Jan C. Nielsen reacted to a post in a topic:
Pending file operation which requires a reboot to complete
Jan C. Nielsen reacted to a post in a topic:
Pending file operation which requires a reboot to complete
-
 Jan C. Nielsen reacted to a post in a topic:
How to run a script if there is a "Reboot Pending" notification
Jan C. Nielsen reacted to a post in a topic:
How to run a script if there is a "Reboot Pending" notification
-
Dev2 Triage joined the community
-
NAA joined the community
-
Slurrpy joined the community
-
test23 joined the community
-
Any action on specific group or subgroup
Hey @Geko - Thanks for reaching out! While creating a scope, add those specific groups using the Edit context option in Scope page. Ensure this scope is chosen in the report template while running. You can also specify the groups/any other, etc. in Advanced templates -> Applications report in the right pane. (refer to images)
-
Geko started following Any action on specific group or subgroup
- Any action on specific group or subgroup
-
OllieH joined the community
-
euan joined the community
- Earlier
-
Pulseway 9.19: Packed. Stacked. Ready to Work. ⚡
Your IT toolbox just got upgraded. Here are the top features to look out for: 🖥️ Peer-to-Peer Remote Control — now when you remote into Windows machines, Pulseway establishes a direct P2P connection, reducing latency and making your remote sessions much smoother. 🕰️ Ad-hoc Automation Scheduling — with Run Later you can now schedule ad-hoc scripts and workflows to execute at a specific date & time. Perfect for off-hours maintenance without disrupting end users. 🗂️ Hierarchical Automation Structure — a new folder hierarchy for Scripts, Tasks, Workflows & Managed Files. Default system content, pre-built packages, and your own creations are now neatly separated. 📊 Patch Status Page Enhancements — the updated Patch Status page shows live deployment progress per patch and allows you to drill down by device. Instantly see which devices are deployed, pending, failed or waiting for reboot. 📂 Background File Transfer — transfer files and folders across Windows, macOS & Linux — without starting a remote session or bothering the end user. Upload, download or delete files directly from the device card’s storage browser. 📋 Policy Extensions — you can build one master policy and fine-tune it per org, site or group as needed. Managing policies is simpler than ever, with streamlined cloning, importing, and exporting. Read more about these releases here: Release Notes
- Feature Request: Expanded Ticket View That Shows Last Comment
-
 Mariale_Pulseway reacted to a post in a topic:
Feature Request: Expanded Ticket View That Shows Last Comment
Mariale_Pulseway reacted to a post in a topic:
Feature Request: Expanded Ticket View That Shows Last Comment
-
New to Pulseway, is this what I should use to roll out Windows 11 in place upgrades to 80 systems?
@Mudslide03 - It should work, yes. However, we recommend to test it in one computer first. If you need more assistance with this, I'll loop in support😊
-
AaronC changed their profile photo
-
AaronC started following Feature Request: Expanded Ticket View That Shows Last Comment
- Feature Request: Expanded Ticket View That Shows Last Comment
-
-
Error Invalid instance name on the Pulseway App on iPhone
Hey @IceKingFlash - Thanks for reaching out! As the free and pro accounts were sunsetted, the only way to reaccess it is to migrate to a new instance. The information from the old instance will be transferred to the new one. You should've received emails about it as well with the link to migrate. Let me know if you have other questions😊
-
IceKingFlash started following Error Invalid instance name on the Pulseway App on iPhone
-
Error Invalid instance name on the Pulseway App on iPhone
Hi there my name is IceKingFlash. I'm here because my Pulseway app on my IOS iPhone doesn't let me login, it keeps telling me "Error Invalid instance name." I looked on reddit and someone said you guy's cut off the free option so there is no more login page for the app. Is there a way I can relog in without a instance name? I only use Pulseway to shut down, restart, and monitor my PC
-
New to Pulseway, is this what I should use to roll out Windows 11 in place upgrades to 80 systems?
Thanks Mariale, The systems are all capable of running Windows 11. Will this script actually kick off the upgrade after the reboot?
-
-
-
New to Pulseway, is this what I should use to roll out Windows 11 in place upgrades to 80 systems?
Hey @Mudslide03 - Can you check if the machines are Windows 11 compatible? You can run a script using Pulseway automation. However, Windows 11 may require manual intervention, so it might not be achievable using Pulseway automation. You can still try to use the script below: # This function automatically upgrades a Windows 10 device to Windows 11. It cannot be used to roll back a Windows 11 upgrade. write-host "Unblock Windows 11 Upgrade" write-host "==========================================================================" write-host "HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate:" "TargetReleaseVersion","TargetReleaseVersionInfo","ProductVersion" | % { if ((gp "HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate" -ea 0).$_) { write-host "- Located Registry value '$_'. Removing." Remove-ItemProperty "HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate" -Name $_ -Force } else { write-host ": No Registry value '$_' found." } } write-host "- System should no longer be blocking updates to Windows 11." write-host " Reboot the system and re-scan for updates." Please run the script in a test environment before you run in a production environment. Let me know if you need anything else😊
-
Contract for Limited Service Offered to A Client
Hey @Kia_24 - Thanks for reaching out! We do not have contracts based on the number of tickets. As an alternative you could have a fixed price contract. For example, pay $5000 for a month, and then in the description of the contract you can mention on the guidelines that the $5000 will cover 30 tickets and that if there's more tickets then the client will have to pay extra. Also, you could mention what type of activities will be included or handled as Application related tickets , H/W related roles etc. But, it all depends on your negotiation and relationship with your client. Let me know if you need anything else😊
- Microsoft Defender reporting pulsewayhardware.sys as malware
-
Kia_24 started following Contract for Limited Service Offered to A Client
-
Contract for Limited Service Offered to A Client
Hi! I am trying to figure out how to create a contract in Pulseway for a service that offers a limited number of tickets to the client. For example, Service B has a limit of 30 tickets in a yearly contract. If they exceed the number of tickets used, they will be charged for every additional ticket they file. Additionally, I need to track the number of tickets the client has used under the contract. Is there a way or an alternate solution for this in Pulseway? Also, I am trying to understand the type of contract in Pulseway, I tried to research the use of every type of contract, but somehow I am not understanding the manual in pulseway.
-
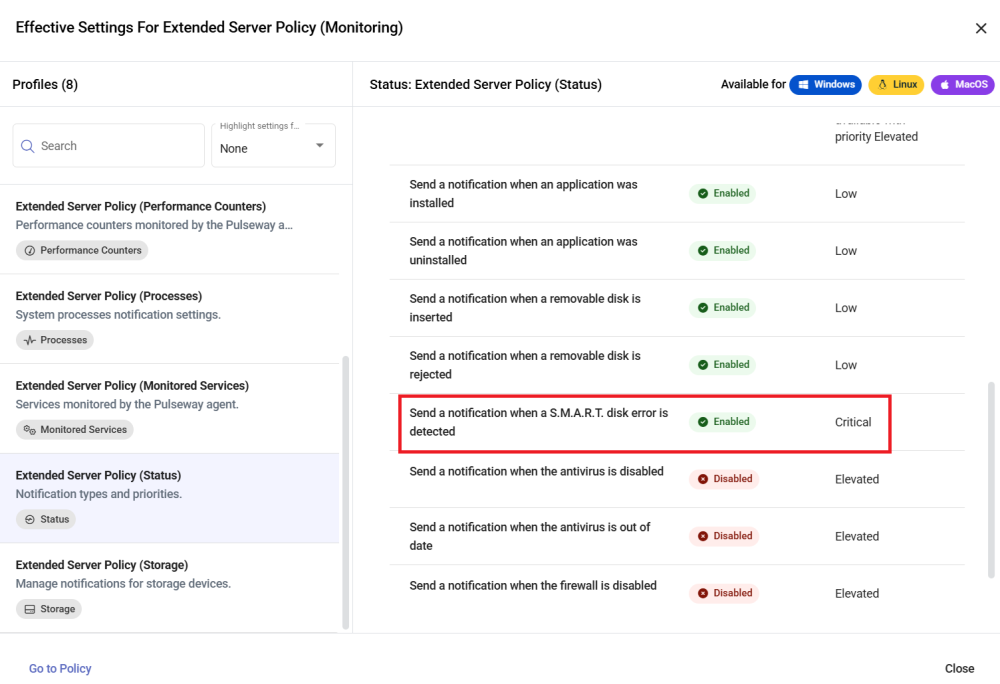
S.M.A.R.T. disk error notification not working
Hey @compsmith - Can you check which monitoring policy is set-up on the device? Navigate to devices > device list > policies Refer to images and let me know!
-
-
New to Pulseway, is this what I should use to roll out Windows 11 in place upgrades to 80 systems?
I am hoping to upgrade in the simplest way possible while preserving data and apps. All systems meet requirements.
-
Microsoft Defender reporting pulsewayhardware.sys as malware
Hello @Mariale_Pulseway , thank you for your reply. What do you recommend I do in the meantime, as Defender keeps detecting the files as malicious and quarantining them? Shoudl I add the "pulsewayhardware.sys" file to eceptions so it stops being flagged? What is the risk asoociated with leaving othe file in place? Does any Pulseway agent functionality break if the file is removed? Thanks!
-
Microsoft Defender reporting pulsewayhardware.sys as malware
Hey @BartB - Thanks for reaching out! We are actively addressing this. Our development team is aware of the associated risks, and a dedicated development effort is underway to completely remove and replace the WinRing0 dependency in a future release. This transition is being prioritized to align with modern security best practices, including Microsoft's Vulnerable Driver Blocklist. In the meantime, please be assured Pulseway runs under a service account and does not expose direct user-accessible interfaces to this driver. If you have any other questions, let me know😊
-
Pending file operation which requires a reboot to complete
Hey @Daniel350 - No worries! Just raised the ticket for you as well😊
-
Pending file operation which requires a reboot to complete
Can you add me to the list of people. Every Server on our account is the same and has been for ages even after multiple reboots
-
S.M.A.R.T. disk error notification not working
Yes it is enabled on all servers and workstations. This particular server has SMART warnings in CrystalDiskinfo, no warnings in Pulseway
-
 bradwillman reacted to a post in a topic:
Microsoft Defender reporting pulsewayhardware.sys as malware
bradwillman reacted to a post in a topic:
Microsoft Defender reporting pulsewayhardware.sys as malware
-
BartB started following Microsoft Defender reporting pulsewayhardware.sys as malware
-
Microsoft Defender reporting pulsewayhardware.sys as malware
Several times now, Microsoft Defender for Endpoint has identified the following file as malware and has quaratined it: Filename: pulsewayhardware.sys Hashes: Hash SHA1 d25340ae8e92a6d29f599fef426a2bc1b5217299 Hash SHA256 11bd2c9f9e2397c9a16e0990e4ed2cf0679498fe0fd418a3dfdac60b5c160ee5 Threat: Winring0 Defender engine version 1.1.25050.6 Defender Mocamp version 4.18.25040.2 VirusTotal link: https://www.virustotal.com/gui/file/11bd2c9f9e2397c9a16e0990e4ed2cf0679498fe0fd418a3dfdac60b5c160ee5 DetectionVirusTotal detection ratio 2/72 Malware detected VulnerableDriver:WinNT/Winring0 Object detailsFile size14.54 KB Is PEtrue IssuerGlobalSign ObjectSign CA SignerNoriyuki MIYAZAKI PE metadataOriginal name WinRing0.sys Company OpenLibSys.org Product WinRing0 Description WinRing0 File prevalenceOrganization devices5 Organization cloud apps0 Worldwide devices10k+ Worldwide observed devices Time First seen Mar 3, 2013 6:00:43 AM Last seen Jun 13, 2025 5:47:56 AM Is this an actual Pulseway file and has anyone else experienced this on any of their agents? What other info can I provide? And before anyone asks, I only deploy agents from the SaaS Pulseway server instance. Thanks, Bart B.
-
Missing modules like Hyper-V, AD, VMWare...
Hey @josheld_65 - Thanks for reaching out! To enable Legacy Mode, run the below Powershell script and open Pulseway manager. Set-ItemProperty -Path "HKLM:\Software\MMSOFT Design\PC Monitor\" AgentLegacyMode -Value 1 Hope this helps 😊
_a9c1b4.png)
_49ee3f.png)
.thumb.png.535cc1ad39ac7ab93df0c3dd3eea25ea.png)
.thumb.png.9b363584f076dd9d66df13f40fea0afe.png)

.png.d2ca142ad393c9ddf45e3a11c46bccfb.png)
.jpg.4581d8b05507172672c130870e9a809d.jpg)