A number of folks have requested the ability to manage bitlocker with Pulseway, so I thought I would share how I am doing this with Powershell scripts and Pulseway's custom fields feature.
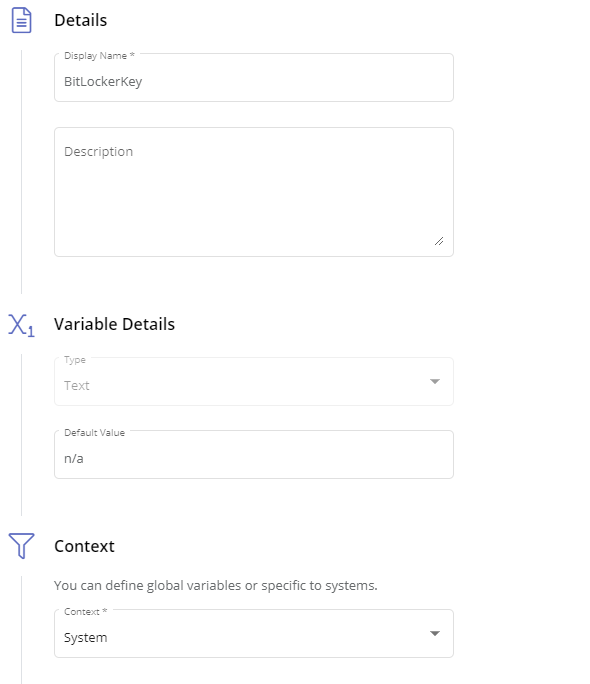
First, you will need to create a custom fields in Pulseway (Automation Tab --> Custom Fields). This fields should be a text variable that has the system context. I personally have 3, BitlockerKey, Protection Status (On/Off), and BitLockerVolumeStatus. BitlockerKey is probably the one most people will care about. .
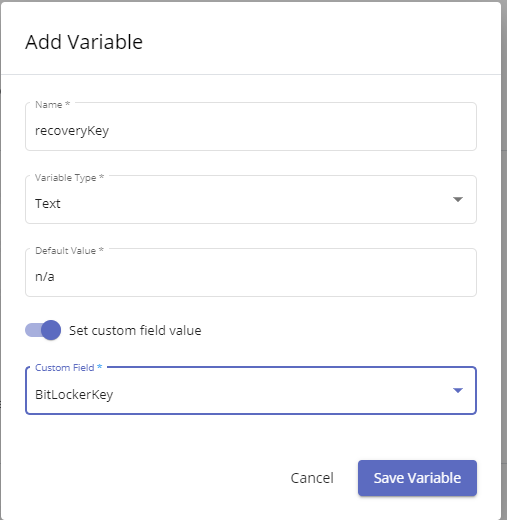
After Configuring the Custom fields, you will then need to create your PowerShell script. Notice you have inputs and outputs. You will want to click New for output. Name it what you wish, ensure it is a text variable type, and then turn on "set Custom Field Value"
Now we toggle the flag for it being a windows powershell script. You should see in the top that it has created a comment #outputs with your defined output variable assigned the default value you gave it.
Now we have our script: Update as of 4/18/2021, script now tracks 3 custom fields and will account for if a drive is encrypted but protection is off and no protectors have been added yet.
# Outputs
$ProtectionStatus = "na"
$recoveryKey = "na"
$VolumeStatus = "na"
#region functions
function Start-BitlockerEnable {
Enable-BitLocker -MountPoint c: -EncryptionMethod XtsAes128 -UsedSpaceOnly -TpmProtector
$today = Get-Date
$scheduledtime = $today.Date.AddHours(23)
[int]$SecondsToMidnight = ($scheduledtime - $today).TotalSeconds
shutdown /r /t $SecondsToMidnight
msg.exe * "Bitlocker Encryption has been enabled. A reboot is needed before the encryption will apply and has been scheduled for $scheduledtime local time. You can reboot before this if you prefer."
#start-sleep 90
#msg.exe * "This Computer will reboot in 30 seconds to bitlocker Encryption"
#start-sleep 30
#Restart-computer -force
}
#endregion functions
#region execution
$BitLockerStatus = Get-BitLockerVolume -MountPoint c:
if ((Get-Tpm).tpmpresent -eq $true) {
#If Volume is in the process of encrypting or decrypting the Volume status will not say fully. Don't make changes when it changes
if (($BitLockerStatus.ProtectionStatus -match 'off') -and ($bitlockerstatus.VolumeStatus -notmatch 'progress')) {
#NoBitlocker is enabled so run it.
if ($BitLockerStatus.VolumeStatus -eq 'FullyDecrypted') {
$recoverykey = $BitLockerStatus.KeyProtector | Select-Object -ExpandProperty recoverypassword
if(!($recoveryKey)){
Add-BitLockerKeyProtector -MountPoint c: -RecoveryPasswordProtector
}
$newStatus = Get-BitLockerVolume -MountPoint c:
$recoverykey = $newStatus.KeyProtector | Select-Object -ExpandProperty recoverypassword
Start-Process -FilePath "$env:PWY_HOME\CLI.exe" -ArgumentList ("setVariable recoverykey ""$recoverykey""") -Wait
if ($newStatus.KeyProtector -match 'Recovery') {
Start-BitlockerEnable
}
}
#Bitlocker must be Partially enabled where drive is fully encrypted, but protection is off and no protectors exist.
#Typically this is using xtsAES128 so you may wish to disable-bitlocker, then re-enable it with your protectors and prefered encryption level.
else{
Disable-BitLocker -MountPoint 'c:'
$decryptInProgress = $true
While($decryptInProgress -eq $true){
$decryptstatus = Get-BitLockerVolume -MountPoint 'c:'
if($decryptstatus.VolumeStatus -match 'progress'){
Start-Sleep 2
}
else{
$decryptInProgress = $false
}
}
Add-BitLockerKeyProtector -MountPoint c: -RecoveryPasswordProtector
$newStatus = Get-BitLockerVolume -MountPoint c:
$recoverykey = $newStatus.KeyProtector | Select-Object -ExpandProperty recoverypassword
Start-Process -FilePath "$env:PWY_HOME\CLI.exe" -ArgumentList ("setVariable recoverykey ""$recoverykey""") -Wait
if ($newStatus.KeyProtector -match 'Recovery') {
Start-BitlockerEnable
}
}
}
#BitLocker should already be enabled so log keys, volume status etc.
else {
$recoverykey = $BitLockerStatus.KeyProtector | Select-Object -ExpandProperty recoverypassword
$ProtectionStatus = $BitLockerStatus.ProtectionStatus
$VolumeStatus = $BitLockerStatus.VolumeStatus
Start-Process -FilePath "$env:PWY_HOME\CLI.exe" -ArgumentList ("setVariable recoverykey ""$recoverykey""") -Wait
Start-Process -FilePath "$env:PWY_HOME\CLI.exe" -ArgumentList ("setVariable ProtectionStatus ""$ProtectionStatus""") -Wait
Start-Process -FilePath "$env:PWY_HOME\CLI.exe" -ArgumentList ("setVariable VolumeStatus ""$VolumeStatus""") -Wait
}
}
else {
$recoverykey = 'NoTpm'
Start-Process -FilePath "$env:PWY_HOME\CLI.exe" -ArgumentList ("setVariable recoveryKey ""$recoveryKey""") -Wait
}
#endregion execution
You can modify the above script as you wish. I personally have gone with a bit of a cautious approach where it will not skip the hardware check which will reboot the pc, but for me I prefer this approach to having it encrypt the drive without checking tpm is all good which could then result in the drive being encrypted and locking out the end user.
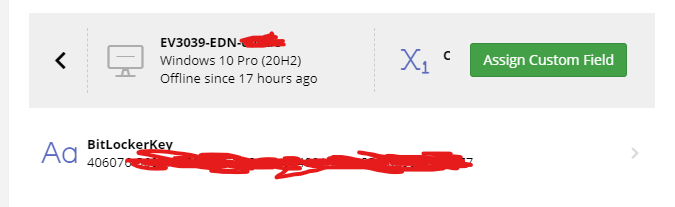
At the end of all this, you now should be able to Both Enable bitlocker encryption as well as pull your recovery keys from pulseway like so :


_a9c1b4.png)
_49ee3f.png)