
Posts posted by David
-
-
-
-
-
-
-
-
-
@Paul My patch policy for the 3rd-party patching trial is ""keep up to date if already installed" for all apps but I'm getting these logs.
-
-
-
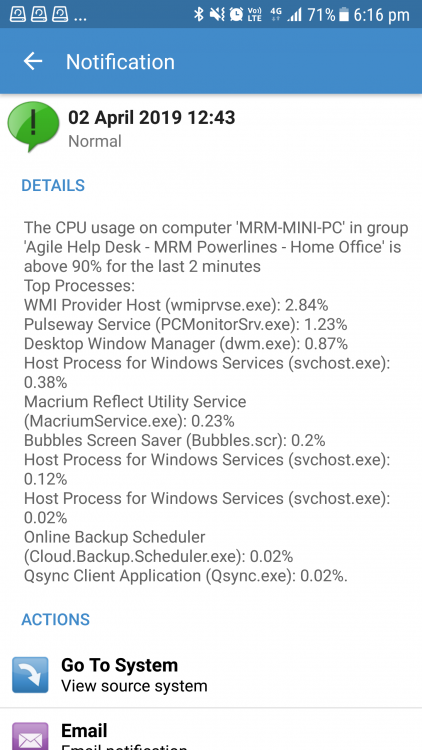
I have this feature set to trigger a notification upon > 90% CPU load for 2 minutes... however, the list of running processes that are returned with this notification are always very low CPU usage (< 5%).
This suggests that either the Pulseway agent is not monitoring ALL running processes or it is not measuring CPU load correctly...?
-
There seems to be a delay in the Web-App AntiVirus section (Kaspersky Lab agent integration). Yesterday I received a notification that multiple threats had been detected on a client machine. Today, these threats do not appear in the "Events" tab or the "History" tab.
My understanding is that "Events" are threats that have not been dealt with yet, whereas "History" is threats that have either been quarantined or deleted... Therefore, based on the applied Group Policy, these threats should be quarantined and should appear in the "History" tab...?
This is not the first time I've noticed this delay. What am I missing?
-
-
-
-
-
On 2/22/2019 at 5:14 AM, Chris said:
Hi @David,
Currently Pulseway can notify you as soon as the certain notification is written into the Windows event log. For more details about this please check out the following article. Also we have the Plugin which can check for some startup events from the systems log.
Thanks, Chris. I was more interested in a search functionality within the web-app Event Log, to make regular triage work more powerful.
-
-
-
-
-
-
Hi,
Policies --> Policy Editor --> Notifications --> Event Log
To then edit a specific filter, the button does nothing at all...
Regards,
-
Hi,
after de-activating the user account for a temporary contract technician, he was still receiving notifications on his iPhone. It was only after disabling PUSH notifications for his account, that they stopped...
I assume all notifications should stop once a user account is de-activated?
Regards,
_a9c1b4.png)
_49ee3f.png)
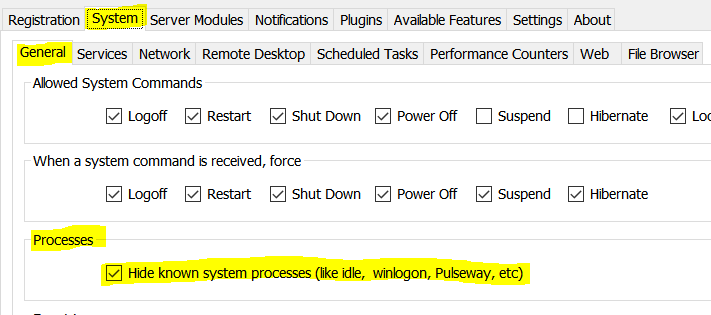
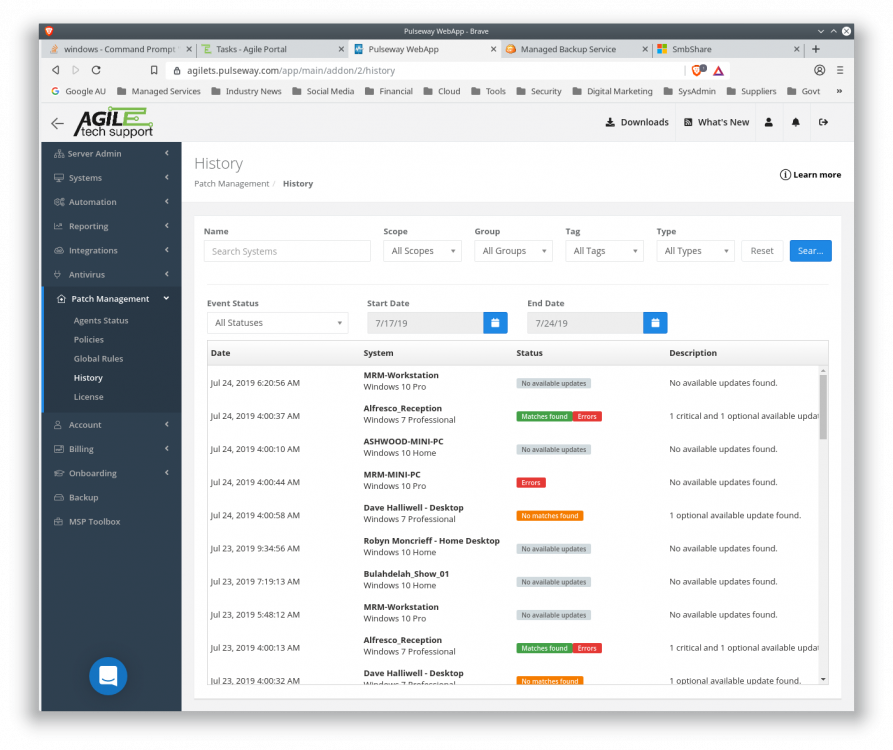
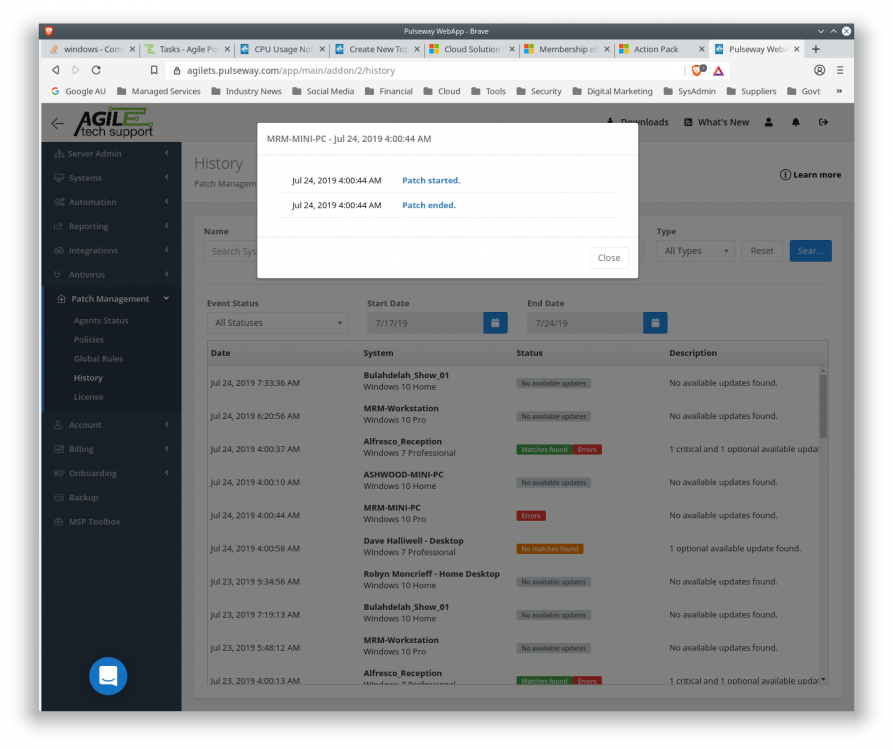

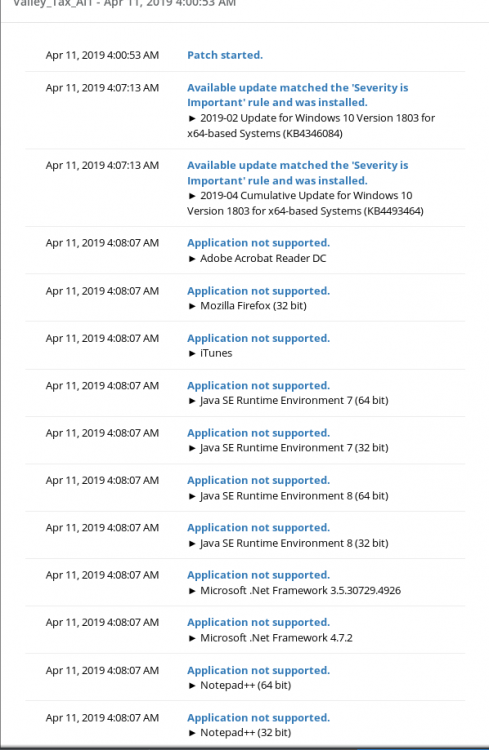



How to change Runtime Powershell credentials/password
in General
Hi @Chris,
How would you set the "PowerShellUserImpersonationPassword" and "PowerShellUserImpersonationPasswordCtrl" across multiple hosts? You would need to use the same admin password across all hosts?
I'm guessing these are a hash result and hash function input?
Thanks,