-
-
Run script before and after running patching policy
Further to this, the suggested solution wouldn't work for us as not all of our machines will be online all the time when our patching policy runs. As discussed here, the automation tasks do not allow for running a task next time the machine is online as the patch policy does. Additionally, the pulseway patching reports do not capture any information about patches that are installed via scripts.
-
Option to set automation tasks to run next time the agent is online
Hi Chris Could you please elaborate as to why the option was removed - If it is an option that can be disabled ie the script runs now and does not run next time the computer is online (like that checkbox appears to be) then I'm not sure I see any reason why that option would have been removed. It would appear functionality was removed with no benefit?
-
Run script before and after running patching policy
Hi Chris, Thanks for your response - to clarify I am using the built in patch management policies not the powershell script to install updates. I'd like to avoid writing a powershell script to perform a function that is already built into the tool. Can the patch management policies be tied into automation tasks? Thanks.
-
Option to set automation tasks to run next time the agent is online
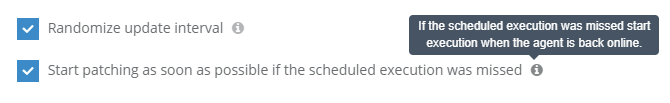
We are using several powershell scripts to set things locally for pulseway as we cannot do this (on a large scale) through the web interface or dashboard - ie set the group name for a whole scope of machines Our automation task works great for this, but only when computers are online. If a machine is offline when the automation task is set to run it does not get the settings. Some computers can go days/weeks without the setting changes. This could be rectified with a checkbox on the automation task, similar to the one on patching policies - see the screenshot below
-
Patching policy history not matching up to actual updates installed
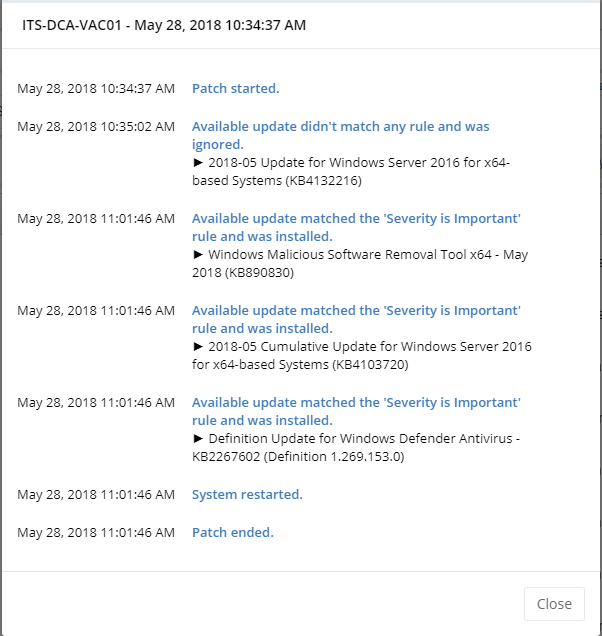
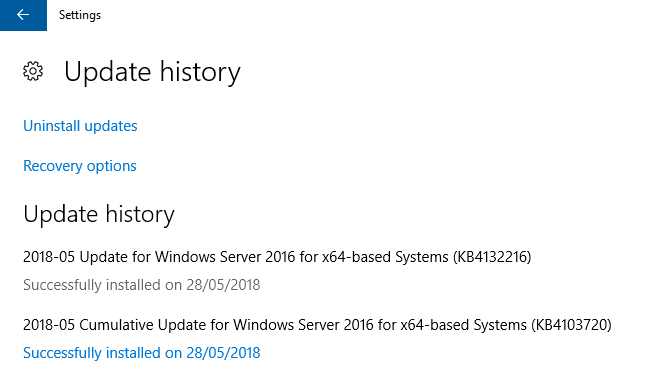
Hi Guys, I'm setting up the patch policies, I've got some strange behaviour - the patching policy history in Pulseway indicates the "Available update didn't match any rule and was ignored." however when logging into the server I can see that update was installed. See the screenshots below - specifically for update 4132216
-
Run script before and after running patching policy
Providing an option to run a script before and after running a patching policy will significantly increase the versatility of Pulseway's patching - A few things we would like to do with this ability include Enable Pulseway maintenance mode before patching to ensure notifications are suppressed Perform a VMware snapshot of the Server VM before patching Run pre/post health checks such as dcdiag to ensure AD servers are healthy and replicating Allow other application maintenance to be performed in the same maintenance window automatically, ie patch Java/Adobe Disable Pulseway maintenance mode after patching is complete
-
Primary Authentication with external Directory
Where possible, we try to avoid using standalone directories and use our Active Directory for primary authentication. I'm sure it would pose a number of technical limitations due to the way Pulseway agents connect to the server, but it would be great if our techs could login to the pulseway server with their AD credentials - either a direct LDAP call or Authenticating through a radius server (the latter opens up the opportunity for lots of MFA vendors as most support MFA via radius).
-
Multi Factor Authentication
I can see Multi Factor Authentication is listed on the roadmap for this year, I was just wondering if you are able to shed some light as to what Multi Factor Authentication options will be available. Ideally, we would love to see integration with Duo Security.
PseudoIT
Members
-
Joined
-
Last visited
_a9c1b4.png)
_49ee3f.png)